Advertisement network installing Android FakeAV (Mobile Defender) |
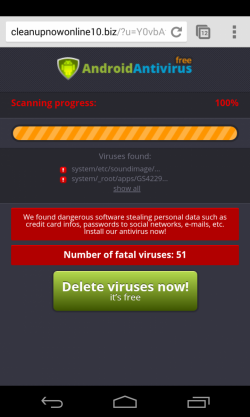
One month ago I was trying to find a streaming site to watch a Spanish soccer match and I found futbolenvivoaldia.com. It was a redirection to the famous site Tarjeta Roja, but the interesting thing was that when I browsed the site with my mobile phone I saw the typical Antivirus scanner saying that my device was infected. Also, an app called “androidav_free.APK” (24f0a666a714e26c6c07ab407e37b112) was trying to be downloaded to my device.
The source of this fake page was one of the advertisement networks of the site tarjetaroja.eu, Mobicow. After some redirections and some tracking URLs this network was returning the following URL to the user's browser:
hxxp://cleanupnowonline10.biz/?u=Y0vbAf0fW9lIhVAxPi2nZQo
This page was loading Javascript code from here:
hxxp://cleanupnowonline10.biz/js/wapc.js
The code was obfuscated and this was the second stage of Javascript code:
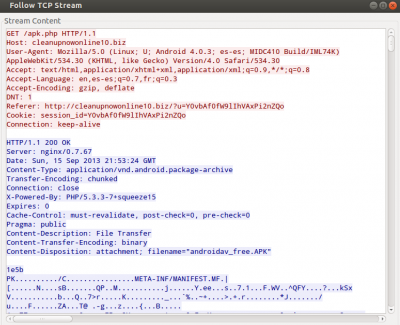
Taking a look at the script content we can see that it contains all the functions necessary to show the fake infection page to the user. Also, we can see that the following URL was used to download the app:
hxxp://cleanupnowonline10.biz/apk.php
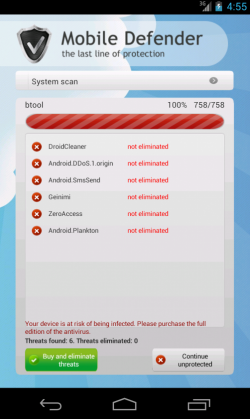
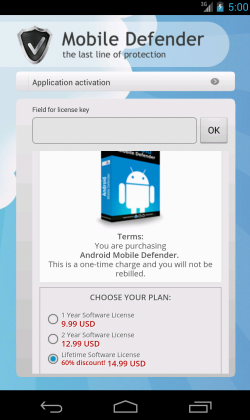
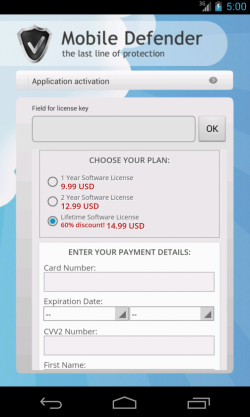
After installing the app we see Mobile Defender, a nice rogue app which will try to scare the users in order to make them buy the “pro” version. A lifetime license just 15$, what a bargain! ;p
The problem is that the application is a bit too persuasive and makes difficult the use of the device by its owner due to the fake Antivirus results. We can say that it is the mobile version of a mix between a FakeAV and a ransomware.
After analyzing the files within the APK file we can see two interesting XML files. One of them is the description of the malware that the app is able to “detect” (“VirusesDescription.xml”). In this file we can find malware information in English and Russian, so we can assume that the origin is probably Russian.
<item>
<id>1</id>
<name>Trojan-SMS.AndroidOS.FakePlayer</name>
<type>Trojan</type>
<description>Маскируется под медиаплеер и после установки рассылает смс по платным номерам</description>
<description_en>Disguises itself as a media player; once installed, sends messages to toll numbers.</description_en>
</item>
<item>
<id>2</id>
<name>Geinimi</name>
<type>Spyware</type>
<description>Собирает информацию об устройстве и отправляет его на удаленный сервер</description>
<description_en>Collects information about the device and sends it to a remote server</description_en>
</item>
<item>
<id>3</id>
<name>Android.Plankton</name>
<type>Spyware</type>
<description>Считывала данные устройства (ID устройства, версия SDK, сведения о привилегиях файла), передает эту информацию на удаленный сервер</description>
<description_en>Reads the device data (device ID, SDK version, file privilege data), passing the information to a remote server</description_en>
</item>
The second interesting XML file is “AffiliateSettings.xml”. It contains the URL visited when the app is executed (“statsapi”) and also the URL used to send the credit card details in order to pay for the “pro” version ("buysite"):
<root>
<affid><![CDATA[84700]]></affid>
<statsapi><![CDATA[http://219.235.1.127/api/dom/no_respond/?group=amd&ver=0001&ts=5cebbc77472874c38b9531da2d83cb32478782c4&token=fya14oiYU]]></statsapi>
<buysite><![CDATA[http://pdblprotect.com/p/?group=amd&ver=0001&ps=$devtype$]]></buysite>
</root>
The app certificate was issued the 10th of August 2013 (Aug 10 17:15:36 2013 GMT) and the date when the package was created was the 15th of September 2013. The package name is com.example.androiddefender2.
As a curiosity and in order to legitimate this application I am showing the code used to analyze the device looking for malware:
this.countViruses = SystemFunctions.generateRandomCountVirus(4, 9);
if (this.countViruses > 0)
{
this.indexesVr = SystemFunctions.generateVirusForIndex(this.countViruses);
AppSingleton.getInstance().getDB(getApplicationContext());
}
Nice, eh? ;) Remember that paying is not an option, because you are not sure if the license is going to work or not. In this case, the app will continue annoying you even if you pay. You can proof this by entering the activation code, hardcoded in the app:
public String activation_code = "7152";
It seems that the advertisements published in well-known sites were not the only way to distribute this malware, but also through SPAM campaigns:
http://www.fireeye.com/blog/technical/2013/09/android-malware.html
http://garwarner.blogspot.nl/2013/09/fake-av-malware-hits-android.html
You can see here additional information about the domains/IPs related to this malware.