ZeuS is still the talk of the town. It's downloaded through fake antivirus, downloaders and several exploit kits. Of course, the best-known social networking site couldn't be out of this. Last week we could see some Facebook messages like the following:
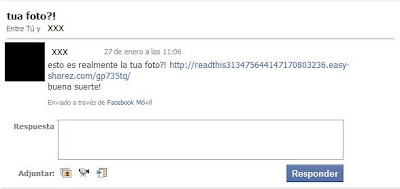
The link in the message would take the users to a Facebook phishing page where they were requested to authenticate. Simultaneously, obfuscated Javascript code was being executed, creating a hidden iframe in the page body:
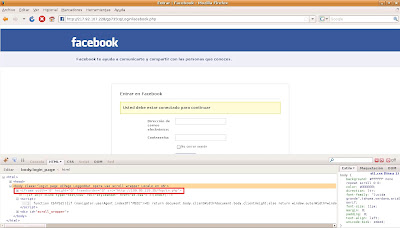
This iframe redirected the user to another web page with two more iframes:
<iframe g1g="321" src="xd/pdf.pdf" l="56" height="31" width="13">
<iframe g1g="321" src="xd/sNode.php" l="56" height="31" width="13">
After advancing further, we arrived to a directory listing in the same server: