Released peepdf v0.3 |
After some time without releasing any new version here is peepdf v0.3. It is not that I was not working in the project, but since the option to update the tool from the command line was released creating new versions became a secondary task. Besides this, since January 2014 Google removed the option to upload new downloads to the Google Code projects, so I had to figure out how to do it. From now on, all new releases will be hosted at eternal-todo.com, in the releases section.
The differences with version 0.2 are noticeable: new commands and features have been added, some libraries have been updated, detection for more vulnerabilities have been added, a lot of bug fixes, etc. This is the list of the most important changes (full changelog here):
-
Replaced Spidermonkey with PyV8 as the Javascript engine (see why here).
-
New command “vt_check” to show VirusTotal detection (API key included). The sample is not sent to VT just hashes.
-
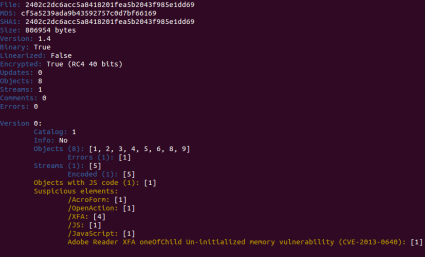
Added detection for CVE-2010-0188, CVE-2010-2883, CVE-2013-0640, CVE-2013-2729 and CVE-2013-3346.
-
Updated colorama to version 3.1.
-
New option to avoid automatic execution of Javascript code (-m). Useful to avoid endless loops related to heap spraying.
-
New command “js_jjdecode” to decode Javascript code using the jjencode algorithm.
-
New command “js_vars” to show the variables defined in the Javascript context and their content.
-
More complete description of the exploits found.
Another change in this version is that it is not possible to use the command “set output” to redirect the output from the interactive console anymore. Some time ago I added the command-line-like redirection (">", ">>", "$>" y "$>>"), so the command “set output” was not longer useful and a bit deprecated.
Besides this, it is important to highlight that a bug related to the interactive console prompt was fixed. The history commands were being truncated and messed up in Unix systems, due to the use of the GNU Readline library and a bug related to not handling colorized prompts correctly. Well, it was partially fixed, because, although it works well in Linux systems, machines running Mac OS X keep having the same issue. The problem is that this operating system uses Editline instead of GNU Readline to manage the interactive console and it seems they don't have a fix for this. If someone knows a workaround to solve this, please contact me, you will make me happy ;)
I am already thinking in the new version, including detection for more exploits/vulnerabilities, JSON output (it seems that XML is not cool anymore, or some years ago ;p), improvements in the execution of Javascript code and fixes for the new bugs found.
If you don't have peepdf in your system it is possible to download the package here (ZIP or TAR.GZ). As usual, I wait for your feedback and your bug reports to continue improving the tool. Thanks a lot!