PDF Attack: A Journey from the Exploit Kit to the Shellcode |
BlackHat USA 2013 is here and tomorrow I will be explaining how to analyze exploit kits and PDF documents in my workshop “PDF Attack: From the Exploit Kit to the Shellcode” from 14:15 to 16:30 in the Florentine room. It will be really practical so bring your laptop and expect a practical session ;) All you need is a Linux distribution with pylibemu and PyV8 installed to join the party. You can run all on Windows too if you prefer.
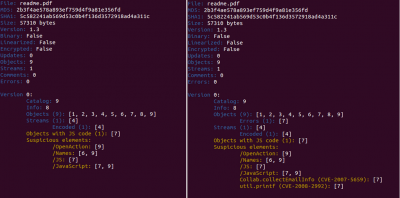
Now Spidermonkey is not needed because I decided to change the Javascript engine to PyV8, it really works better. Take a look at the automatic analysis of the Javascript code using Spidermonkey (left) and PyV8 (right).
If you want to install the setup in your own system you can follow these instructions by Xanda to install pylibemu and to get PyV8 ready just install some dependencies (libboost-python-dev, libboost-thread-dev and libboost-system-dev) and let pip do the hard work (sudo pip install -v pyv8), it downloads also V8 and sets the environment variables needed, really easy! If it does not work maybe you can also take a look at this blogpost.
Also, I will upload some obfuscated Javascript code and PDF files to play during the session.
And a really cool thing, I will have between 10 and 15 peepdf t-shirts waiting for you in different sizes, take a look and come fast during the break (15:15-15:30) or after the session if you want one ;) If you are late I also have some stickers!! See you tomorrow!!!