New peepdf v0.2 (Black Hat Vegas version) |
Last week I was in Vegas presenting the new release of peepdf, version 0.2. Since my release at Black Hat Amsterdam some months ago I hadn't created a new package so it was time to do it. You can now download the new package here or use “peepdf -u” to update it to the latest version.
So the main new features, besides the fixed bugs, are the following:
-
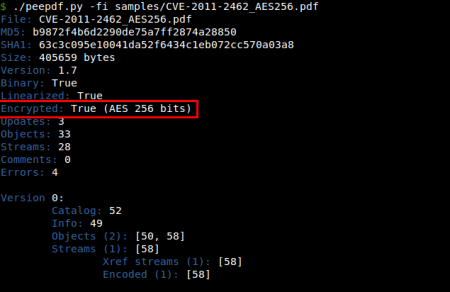
Added support for AES in the decryption process: Until now peepdf supported RC4 as a decryption algorithm but AES was a must. Now here it is, so no more worries for decrypted documents. I will be ready for new changes in the decryption process, someone in Vegas told me that the next AES modification for PDF files is coming...
-
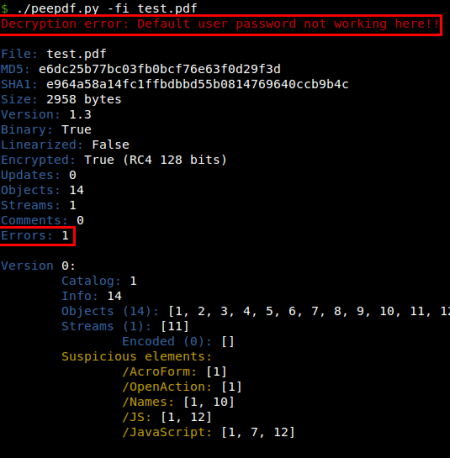
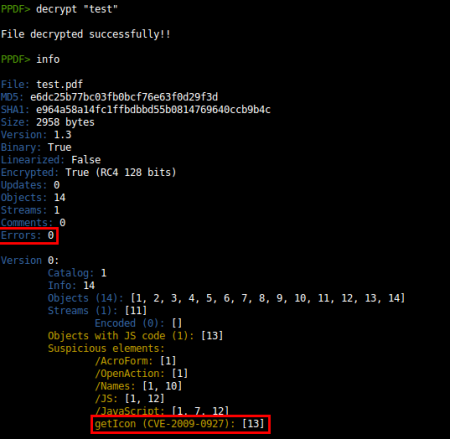
Added decrypt command: The normal way of sending malicious encrypted PDF files is with no user password, so the victims don't need to put any password manually, it uses the “default” blank password to decrypt it. However, in some cases the password was written in the emails body, for instance. For these cases we can use the decrypt command. In a preliminary analysis we see an error that tell us that the password is not correct. But we can use this new command to perform another analysis giving the password used to encrypt the file. This way we can see all the encrypted objects without problems.
-
Shellcode emulation with pylibemu: The shellcode emulation with peepdf was performed with the sctest binary directly. It wasn't that smart so I had in the TODO list taking a look at the alternatives. Thanks to Angelo Dell'Aera, pylibemu author, I've finally included an smarter way to do it, adding pylibemu to the project. The result is very similar but now you won't need the sctest binary but installing pylibemu. Besides this, if the shellcode uses the URLDownloadToFile function, pylibemu will try to download the binary to disk. Also, other of the good things of this change is that I can work with Angelo closely to solve any potential issues :) I recommend using the git repository to update the libemu files and then install the latest version of pylibemu.
-
Added support for HTML entities decoding: One method to obfuscate Javascript code is to encode it with HTML entities. Sascha Weiss shared some samples with me at Black Hat Amsterdam this year (thanks!) and now it's supported and transparent for the user.
-
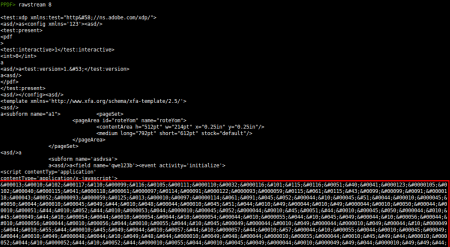
Extraction of Javascript code from XDP packets: When Javascript code is found in a XDP packet (XFA template) normally it's stored in XML format, in a script element. Until now when you executed the js_code command with an XDP object you had the full content, including the script element, but now the JS code is correctly extracted, without garbage.
-
Added support for CCITTFaxDecode filter: One more for the collection of supported filters. Thanks to Binjo this decoding filter is included now, due to the fact that we have seen some malicious files including this type of encoding this year.
-
More colors in the interactive console: I have included more colors in the interactive console to highlight the important elements shown in the info command, like objects containing Javascript code or trigger elements. for example. Also, errors (red) and warnings (yellow) are colorized now. You can always use the -g option (grinch mode) to avoid the colorized output.
You can find the full content of the changelog here. If you find any bug, you have a suggestion or you want to collaborate with the project be free to email me, I will be happy to respond you ;) Also, you can follow the peepdf latest news on Twitter and me, if you want to contact directly.
Finally, I want to say thanks to the Black Hat organization, my employer, S21sec, and, of course, to the Arsenal people (Rachid and Nabil) for letting me go there to show the new features. Also, thanks a lot to all the contributors and people giving me feedback :)