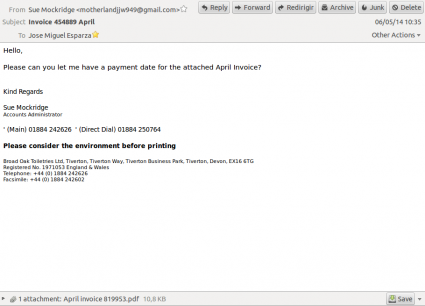
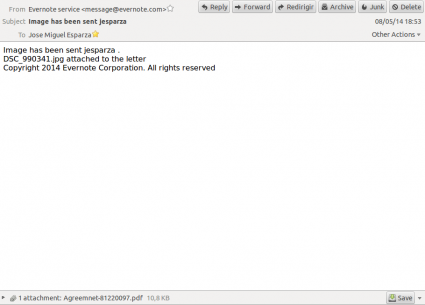
I am used to receive SPAM emails containing zips and exes, even "PDF files" with double extension (.pdf.exe), but some days ago I received an email with a PDF file attached, without any .exe extension and it didn't look like a Viagra advertisement. Weird. I didn't have time to take a look at it, but the next day I received another one, with a different subject. The subject of the first email was “Invoice 454889 April” from Sue Mockridge (motherlandjjw949 at gmail.com) attaching “April invoice 819953.pdf” (eae0827f3801faa2a58b57850f8da9f5), and the second one “Image has been sent jesparza” from Evernote Service (message at evernote.com, but really protectoratesl9 at gmail.com) attaching “Agreemnet-81220097.pdf” (2a03ac24042fc35caa92c847638ca7c2).
At this point I was really curious so I took a look at them with peepdf.
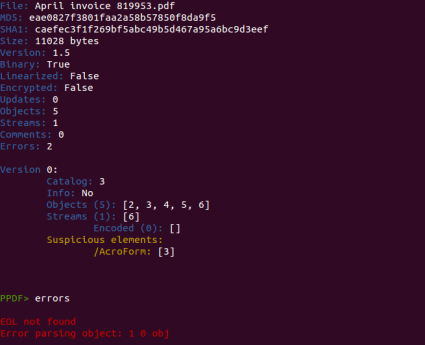
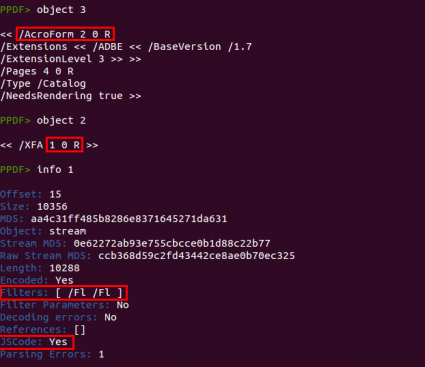
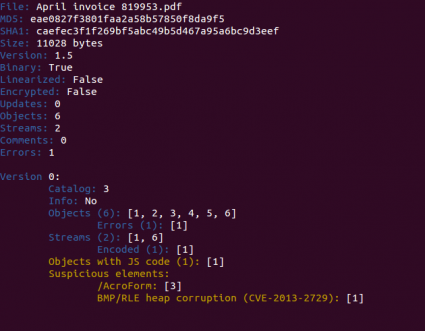
At that moment I only saw a suspicious /AcroForm element, but nothing more. This element was referencing object 1, not shown due to a bug in peepdf.
I had to fix it to see the important stream (object 1), encoded twice with /FlateDecode, but in its abbreviated format ([/Fl /Fl]). It was an XFA form, containing Javascript code and an image encoded in Base64. After extracting the stream to a file it had an unusual size, 85MB. Small, eh? ;) Besides containing four script elements, the culprit of this size was the encoded image, a BMP file with a repeating pattern, “\x00\x02\xff\x00”.
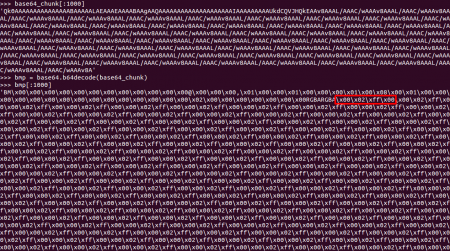
With this information and thanks to other characteristic strings found in this object (
“0aa46f9b-2c50-42d4-ab0b-1a1015321da7”, “// Index of the overlapped string”, “// Base of the AcroRd32_dll”, etc) it was easy to spot the vulnerability exploited here. It turned out to be the
Adobe Reader BMP/RLE heap corruption vulnerability (CVE-2013-2729) and
the bad guys copied the PoC written by Felipe Manzano (it was not the first time that the attackers reused code from
Felipe, for example,
in the case of a CVE-2011-2462 exploit). I have to be fair and mention that the bad guys made some extra effort to add more ROP offsets to cover 23 different Adobe Reader versions, from 9.3.0.3 to 11.0.0.1 ;) The vulnerability itself is an
integer overflow patched one year ago and explained really well by Felipe in these
blog post and
whitepaper, so nothing to add here.
Knowing all the details about the exploit it was easy to make peepdf detect it (update it using the -u flag!):
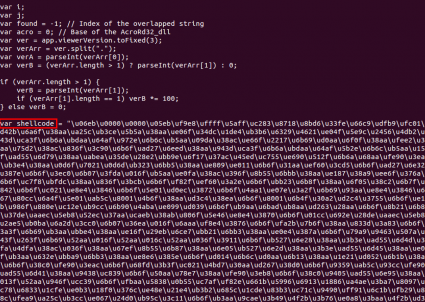
The shellcode was not hidden at all, it was located in plain sight within one of the script elements, so it was easy to decode with the js_unescape command.
In both PDF files the shellcode tried to download an executable from a compromised web site:
hxxp://dr-gottlob-institut.de/11.exe (91aa1168489a732ef7a70ceedc0c3bc9)
hxxp://filling-machine-india.com/images/1.exe (5ce7451cce4593698688bd526bfcec78)
After the execution of the first binary the system was downloading:
hxxp://pgalvaoteles.pt/111 (91d33fc439c64bd517f4f10a0a4574f1)
hxxp://files.karamellasa.gr/tvcs_russia/2.exe (e070ff758c2af2eee89f4a0f50077e30)
The binary 91d33fc439c64bd517f4f10a0a4574f1 was dropping
ZeuS-P2P/Gameover with the Necurs rootkit, but the size was unusually big (496,128 bytes). Inside the rootkit a PDB path related to GMER could be found (“
e:\projects\cpp\gmer\driver\objfre_wxp_x86\i386\gmer.pdb”), probably used to disable the rootkit detection.
After that, another loader was downloaded and executed:
hxxp://www.shu-versicherungsvergleich.de/loader.exe
From this point and after connecting to pimplelotion.com (95.163.104.88) to receive instructions a lot of binaries were executed. This is an example of the configuration received from this server:
<?xml version="1.0"?>
<config>
<interval>10</interval>
<timeout>5</timeout>
<urls>hxxp://95.163.104.88</urls>
<country>Netherlands</country>
<tasks>
<install id="1" filetype="1" name="soks" autorun="1" limits="0:16632" filter="" hash="2368a8c8b50900d57c0366049f755c05">hxxp://segurgestion.es/1.bin</install>
</tasks>
</config>
And the list of URLs I had until I stop monitoring it:
hxxp://adventiaingenieria.es/222
hxxp://segurgestion.es/1.bin
hxxp://golestangallery.com/333%283%29.exe
hxxp://intropitch.com/1.bin
hxxp://regleg.eu/images/777.exe
So it was funny (and weird) to receive directly a PDF exploit via email and not the usual downloader like Andromeda/Upatre to drop ZeuS-P2P/Gameover (among others). Also, it was the first time I was seeing this vulnerability in the wild, because, as far as I know,
it is not used in any Exploit Kit either. If I am wrong and you think this vuln is common be free to drop a comment ;)

i guess i'm the only person
i guess i'm the only person that's genuenly mad about not getting any spam mails
Haha, I will tell my
Haha, I will tell my "friends" to include you in the list too ;p
Got something similar sent to
Got something similar sent to me today.
File: inovice_AUG_4510168.pdf
CRC-32: 70ba5386
MD4: bb3d5904640185a0ff0c2501beaea9c2
MD5: 89839fa52903a365e7933a0e8efe4db7
SHA-1: 7a0f3c1463ca8650e105f5a0082fe2873890bd3a
Hi! Thanks for adding this
Hi!
Thanks for adding this information! ;) Yes, it seems that there are some new campaigns dropping Dyre / Dyreza and adding a bit of obfuscation in the Javascript code...
Hi, Thanks for the article, I
Hi,
Thanks for the article, I helped me understand some internals of malicious PDF files.
I have also received a few of the last PDF exploiting CVE-2013-2729.
One of these can be viewed on : https://www.virustotal.com/en/file/10f0734ccfefc2db770f2aa1fc4d9e86a81c7...
I've tried to de-obfuscate the payload, but didn't manage to find the time/skills to do so.
It would really be great if you can explain how these last PDF droppers works and how to obtain their payload.
Thanks again!
Hi! Thanks for the comment! I
Hi!
Thanks for the comment! I want to publish another blog post before, but I will write something about these other PDF files too ;)
Hello, Thanks for the write,
Hello,
Thanks for the write, but could you share the sample for testing?