Uncovering the "new" Eurograbber: really 36 million EUR? |
Eurograbber is in the news, beware. Some days ago Versafe and Check Point Software Technologies published a “new” threat report titled “A Case Study of Eurograbber: How 36 Million Euros was Stolen via Malware”. A bit sensationalist, yes. If it was well documented and there was real proof of that, I would have nothing to say, but it turns out that this threat is not so new and I wrote about it by the end of September, when I was working at S21sec. I called this Sopelka botnet.
Apart of being new or not (I think all of us thought that we were the first ones when really not), the report throws some data about affected banks/users and, the most important, the amounts stolen from each country by the fraudsters: more than 16 million EUR in Italy, almost 13 million EUR in Germany, almost 6 million EUR in Spain and more than 1 million EUR in Netherlands. In summary, more than 36 million EUR in Europe. Taking into account the sad times we are living in, crisis times, it's pretty noteworthy, isn't it?
This report and, above all, these stolen amounts have been quickly published everywhere and are quite widespread, faster than some of the most infamous Trojans. That's why I would like to say some words about the report and these astonishing amounts:
- It's not a new Trojan, not a new customized ZeuS, it's just Citadel. Citadel, but also Tatanga and Feodo. In this botnet were used at least three different Trojans.
- Nothing really new or innovative in the HTML injects. The two-factor authentication provided by SMS codes was bypassed when the first mobile component was discovered in September 2010. Maybe one new thing was that a third-party SMS service was used directly from the injects to send SMS messages to the victims, but nothing more.
- No new ZitMo variation, even it's not the HTTP sample, it's just the very first version of September 2010 but with less commands, just fordwarding all the SMS received to the admin phone number.
- In "The Money Theft" report section the process is described as if the bad guys must wait for the victim to login and then the transfer is performed in an automatic way. But, really, once the mobile application is installed on the victim's phone they have all the information they need to login by themselves, so they could make the transfer manually and wait for the TAN that will be forwarded to their admin phone. The backend was prepared for automatic transfers but this gang was not using that functionality, there were no details about transfers in the panel.
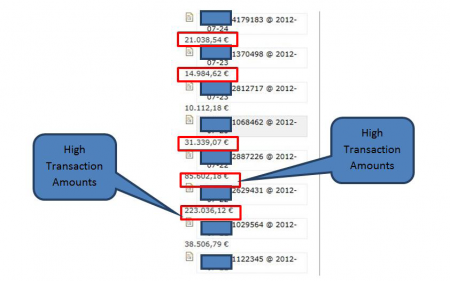
- The "High Transaction Amounts" image shows the stolen amounts, according to the report. However, these amounts are comments written by the bad guys for each account, in this case they are showing accounts balances. In other cases they posted comments like "no valid", "android", socks ip and ports, etc. Just comments to better control these accounts and help to commit the fraud. Based on what we know, it seems that the authors have mistakenly interpreted the logged account balances of victims for transactions, added those balances up and came to the conclusion that it was the most profitable trojan... but actually it is not.
High Transaction Amounts image (Source: Versafe & Check Point report) - The report says that more than 30,000 users were affected, 7 Spanish banks and 3 in The Netherlands. According to my data the affected users number was much lower (almost one third of that number), there were more Spanish banks affected (16), but only one in The Netherlands.
I would like I was wrong with all of this, but all is pointing to a marketing report crossing the line to acquire media attention. Of course this botnet made its profit, but 36 million EUR is not real at all. If the authors can read this post be free to comment here and/or contact me if you think I'm wrong or if you have something to say. If really these amounts are not true I would expect some kind of explanation, scaring people with no reason is not good at all...
I totally agreee with you
I totally agreee with you
Very interesting. We've been
Very interesting. We've been following this story and wondered about the amounts the amounts reported as well. Thanks for posting.