Styx Exploit Kit installing Simda |
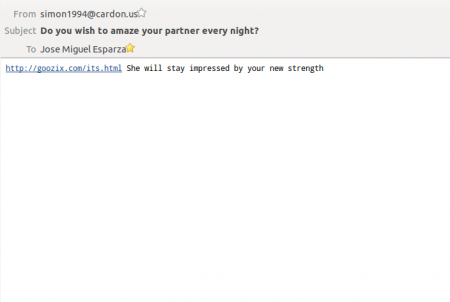
I was already missing these SPAM emails with some advice about my sexual life: “Your woman wants you to be the best lover”, “The greatest technique to gratify your lady”, etc. I was getting upset about this, I needed some help...;p
So finally I am receiving a lot of these again. After visiting the link (hxxp://goozix.com/its.html) we can see a redirection to a page to buy Viagra and other “medicines”. But also there is some malicious Javascript code hidden there. The result of the deobfuscation contains code to create a cookie (“visited_uq=55”) and also an iframe to load the URL hxxp://gylaqim.com/exit.php. This domain, created on the 21st of September, resolves each time to a different IP and has a history of more than 400 IPs. It has 6 authoritative DNS servers, ns*.gylaqim.com, also resolving to multiple IPs.
Depending on the server which is responding after visiting hxxp://gylaqim.com/exit.php we will be redirected to another initial page - with another redirection to a Viagra site plus malicious Javascript code - or to the actual exploit kit.
The initial pages seen until the moment are the following:
hxxp://178.170.104.124/destruction.html
hxxp://178.170.104.124/seed.html
hxxp://actes-lyon.org/true.html
hxxp://aybabtu.ru/express.html
hxxp://brave.net.nz/ocean.html
hxxp://goozix.com/its.html
hxxp://moniwild.sakura.ne.jp/average.html
hxxp://rodinr.511.com1.ru/angle.html
hxxp://southeasterntrains-fail.com/somewhere.html
hxxp://toys-store.net/dawn.html
hxxp://toys-store.net/low.html
hxxp://webhydro.com/copy.html
The URLs leading to the exploit kit have the following format:
hxxp://www3.ad63gyomll2jo237-1.usa.cc/?war0he=mbblKWampZqWdPsrJqgkqbe22%2BWaGVmp5qpaJyYlIg%3D
hxxp://www3.ad63gyomll2jo237-1.usa.cc/?xsp2a4=njZlp5pmpZqWdPsrJqgkqbe22%2BWaGVmqKynapVnlIg%3D
hxxp://www3.ev2okgoe5o6.usa.cc/?9fq8=XdvanKKraGfjdvYcpxqX9rlpKLcY5%2BgmqjHbaZoa4o%3D
hxxp://www3.ev2okgoe5o6.usa.cc/?c37spa463=h6ig12WbWhni%2BKlrJibldmp23PJZGeoo5qWbmqXqFY%3D
hxxp://www3.x-8hlldq1w50.usa.cc/?nxemgrrrxh=ku3O0aSnqSsjuSgdZWgktjlnbSbYZ6tmKbJqqmkqow%3D
hxxp://www3.y-83m4wjpzlx6.usa.cc/?2ef0=VtrPlLZicWWhWuPdraegnqqm0aOWql1tZqaWrGirJA%3D
Once you visit these links you are redirected again towards a “i.html” page:
hxxp://www1.l5yhg95szx7k42.usa.cc/i.html
hxxp://www1.o-6vuo7jzwff5fv.usa.cc/i.html
hxxp://www1.qejt8wkvxre5a98.usa.cc/i.html
hxxp://www1.xjfvtg6bagx8.usa.cc/i.html
hxxp://www1.yi4f59df9s509dmg7.usa.cc/i.html
This page contains the Javascript code to detect the plugins installed in the browser (PluginDetect), an iframe (“crezidf.html”) and more Javascript code to obtain the iframe content and decode it. This simple code makes the deobfuscation dependent on the iframe and, therefore, more difficult to analyze in an automatic way.
After the deobfuscation step:
We can see three different web pages depending on the Java version installed:
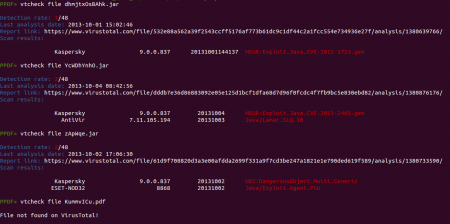
- The web page “jorg.html” downloads the file “dhmjtxOsBAhk.jar” (cba750fafa12d9f53dedac9101d54180), an exploit of the “Java Applet Field Bytecode Verifier” vulnerability (CVE-2012-1723).
- When “jvvn.html” is loaded it tries to download the applet “YcWDhYnhO.jar” (f2a978cce12906af5bb9d91112143a1a) to exploit a security problem in the JRE 2D subcomponent (CVE-2013-2463).
- Finally, when the user is redirected to “jply.html” the file “CxolvGRXM.jnlp” is downloaded to bypass the security warning window and the applet “zApWqe.jar” (5783988184709219c949fba03dead46e) is executed to try to exploit the “Java Applet ProviderSkeleton” vulnerability (CVE-2013-2460).
In the case that there is no Java plugin installed or that the Java version installed does not match with the specified in the code then the “pdfx.html” will be loaded. If the URLs mentioned above could give us an idea about the exploit kit used, after seeing this name, “pdfx.html“, we have no doubts that we are dealing with Styx Exploit Kit.
Similarly to “i.html”, “pdfx.html” also loads an iframe (“mbahsldw.html”) and some Javascript code to decode the iframe content. The second stage of Javascript code was this:
Here we can see that the “fnts.html” page will be loaded in the case that the browser is Internet Explorer and the system is not a 64-bit platform. Then this page also downloads the file “bXwOlglw.eot” (51f2ae12128ee8115f65e2657e6afddc) to exploit the “TrueType Font Parsing” vulnerability (CVE-2011-3402). Besides of this, depending on the Adobe Reader version installed the file “KummvICu.pdf” (2a4e488c0ef620482ae93778249b4447) will try to exploit the TIFF vulnerability (CVE-2010-0188) or we will be redirected to “retn.html”. This page was returning a 404 code at the moment of the analysis. Apparently, a real 404 code ;)
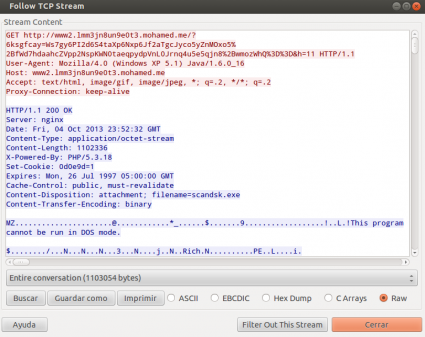
If any of the exploits succeed then a big binary (1,1MB) with name "scandsk.exe" (6ee26e3783a45aa22b8541b681bc5643) is downloaded from a URL similar to the following and executed.
hxxp://www2.lmm3jn8un9e0t3.mohamed.me/?6ksgfcay=Ws7gy6PI2dMOxo5%2BfWd7hdaahcZtaeqpydpVnL0Jrnq4u5e5qjn8%2BwmozWhQ%3D%3D&h=11
After being executed something was not working properly, because the created process was using 100% of the CPU:
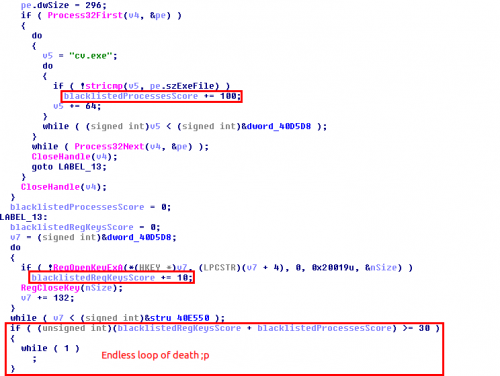
Then it was time to take a look at the memory of the process with Olly. A suspicious section with executing permissions was easily spotted, containing some binary files. Taking a look at one of them with IDA we could see a lot of strings and the reason of this huge CPU usage: an infinite loop due to the detection of some process in execution.
As you can see, this function adds 100 "points" each time a process in execution matches with the blacklisted processes and 10 "points" when one of the blacklisted registry keys exist in the system. If the final score is greater than 20 then it goes to an endless loop. These are the blacklisted processes:
cv.exe
irise.exe
IrisSvc.exe
wireshark.exe
dumpcap.exe
ZxSniffer.exe
Aircrack-ngGui.exe
observer.exe
tcpdump.exe
WinDump.exe
wspass.exe
Regshot.exe
ollydbg.exe
PEBrowseDbg.exe
windbg.exe
DrvLoader.exe
SymRecv.exe
Syser.exe
apis32.exe
VBoxService.exe
VBoxTray.exe
SbieSvc.exe
SbieCtrl.exe
SandboxieRpcSs.exe
SandboxieDcomLaunch.exe
SUPERAntiSpyware.exe
ERUNT.exe
ERDNT.exe
EtherD.exe
Sniffer.exe
CamtasiaStudio.exe
CamRecorder.exe
And the blacklisted registry keys:
Software\\CommView
SYSTEM\\CurrentControlSet\\Services\\IRIS5
Software\\eEye Digital Security
Software\\Microsoft\\Windows\\CurrentVersion\\Uninstall\\Wireshark
Software\\Microsoft\\Windows\\CurrentVersion\\App Paths\\wireshark.exe
Software\\ZxSniffer
Software\\Cygwin
Software\\Cygwin
Software\\B Labs\\Bopup ObserverAppEvents\\Schemes\\Apps\\Bopup Observer
Software\\B Labs\\Bopup Observer
Software\\Microsoft\\Windows\\CurrentVersion\\Uninstall\\Win Sniffer_is1
Software\\Win Sniffer
Software\\Classes\\PEBrowseDotNETProfiler.DotNETProfiler
Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MenuOrder\\Start Menu2\\Programs\\Debugging Tools for Windows (x86)
SYSTEM\\CurrentControlSet\\Services\\SDbgMsg
Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MenuOrder\\Start Menu2\\Programs\\APIS32
Software\\Syser Soft
Software\\Microsoft\\Windows\\CurrentVersion\\Uninstall\\APIS32
Software\\APIS32
Software\\Microsoft\\Windows\\CurrentVersion\\Uninstall\\Oracle VM VirtualBox Guest Additions
SYSTEM\\CurrentControlSet\\Services\\VBoxGuest
Software\\Microsoft\\Windows\\CurrentVersion\\Uninstall\\Sandboxie
SYSTEM\\CurrentControlSet\\Services\\SbieDrv
Software\\Classes\\Folder\\shell\\sandbox
Software\\Classes\\*\\shell\\sandbox
Software\\SUPERAntiSpyware.com
Software\\Classes\\SUPERAntiSpywareContextMenuExt.SASCon.1
Software\\SUPERAntiSpyware.com
Software\\Microsoft\\Windows\\CurrentVersion\\Uninstall\\ERUNT_is1
In the same anti-analysis function they are also checking if the process is being debugged, if Sandboxie is executing, etc. In the case that the file “c:\\cgvi5r6i\\vgdgfd.72g” exists and that it contains certain bytes then the other checks are not necessary. With this information we can already say that the binary is a version of Simda.
This sample, among other things, is able to send some information about the system to its control panels: system language, operating system, ProductId, etc.
wv=%s&uid=%d&lng=%s&mid=%s&res=%s&v=%08X
Depending on the request type this information is included or not within the following parameters:
controller=hash&mid=
controller=sign&data=%s&mid=%s
Then these parameters are decoded and added as the value of a two-character parameter:
"?%c%c=%s"
Both of these are HTTP GET requests, using a hostname with the format "update%s.%s.com" and the following User-Agent:
Mozilla/5.0 (Windows NT 6.1; WOW64; rv:2.0b8pre) Gecko/20101114 Firefox/4.0b8pre
The hardcoded IPs where these requests are sent depend on the request type too:
212.117.176.187 (hash)
79.133.196.94 (sign)
69.57.173.222 (sign)
Another request type uses more than two characters as the parameter name but it also encodes the system information as the value of this parameter. In this case the hostname has a different format (report.93aaaaaa9ku7m3g793k.com ,for instance) and the User-Agent is different too:
Mozilla/4.0 (compatible; MSIE 8.0; Trident/4.0; .NET CLR 2.0.50727; .NET CLR 1.1.4322; .NET CLR 3.0.04506.590; .NET CLR 3.0.04506.648; .NET CLR 3.5.21022; .NET CLR 3.0.4506.2152; .NET CLR 3.5.30729)
Other parameters seen in the binary content are the following:
/?abbr=RTK&setupType=update&uid=%d&ttl=%s&controller=microinstaller&pid=3
Among a lot of other functionalities, this malware is capable of modifying the hosts file to redirect the traffic of the infected machine, modifying the search engine of Internet Explorer and Firefox to findgala.com, modifying the desktop “My Computer” shortcut, disabling the User Account Control (UAC), etc, etc. Some sources say that it can also act as a banking malware, but I have not seen any proof of that in this sample. If you want to read more abut this malware family take a look at the following links:
http://malwaremustdie.blogspot.nl/2013/02/hulk-and-malware-crusaders-vs-fakeav.html
https://pastebin.com/zZ9nKEVP
http://www.virusradar.com/Win32_Simda.B/description