BlackHole leading to Feodo: Bank of America account frozen |
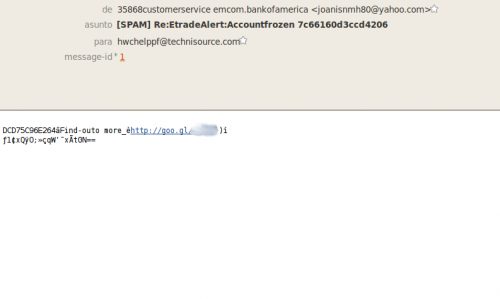
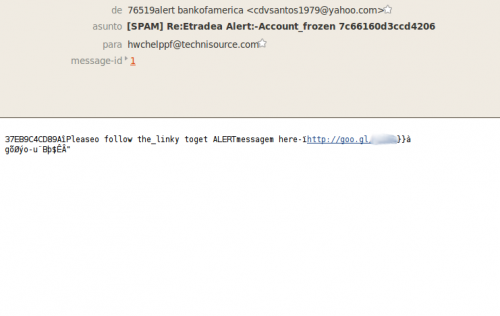
I've received a Christmas gift some hours ago. In fact there were two gifts but only one has survived the trip. They are from Russia...with love. Of course I'm talking about two e-mails I've received with two suspicious links. Even the e-mail bodies were suspicious, I think they have packed very quickly my gifts or they are not very attentive to me...:( The From field included "bankofamerica" and the Subject "Accountfrozen" so I suppose this means that my Bank of America account is frozen, right?
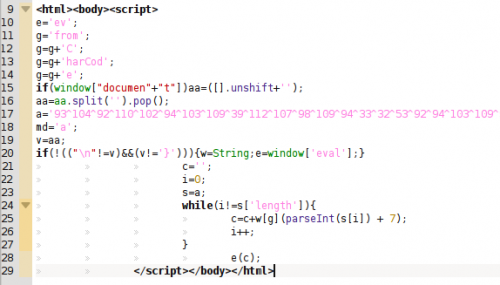
After some redirections we can find the typical obfuscated Javascript code made in BlackHole:
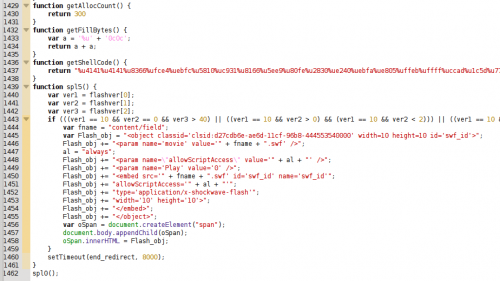
After decoding the Javascript code we obtain the next step, also related to BlackHole. This time I can only see a unique Flash exploit trying to download and execute a binary from the same domain where the exploit kit is located (shellcode is XORed with 0x28).
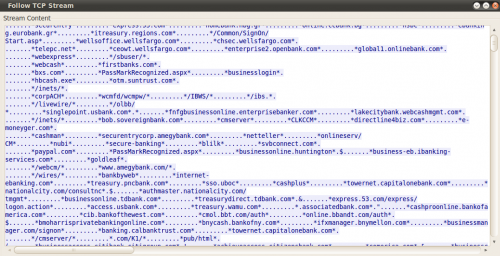
The binary, downloaded from a URL with format http://domain/w.php?f=18&e=6, has a very low detection rate (5/43) and it's identified as a generic Downloader. If we take a closer look at its network traffic we can see some interesting strings:
Because of this and other strings, like HTML code asking for credentials, we can say that we have a banker here and Feodo is its name. The related domains have been registered with Russian identities this week (some of them today) and their IP addresses also belong to Russian net-blocks:
Registrant ID:DI_20058793
Registrant Name:Maksim Karpov
Registrant Organization:N/A
Registrant Street1:Kozlova 38/33
Registrant Street2:
Registrant Street3:
Registrant City:Vsevolojsk
Registrant State/Province:
Registrant Postal Code:346940
Registrant Country:RU
Registrant Phone:+7.4955259668
Registrant Phone Ext.:
Registrant FAX:
Registrant FAX Ext.:
Registrant Email:heavi@bk.ru
It's not new, BlackHole leading to ZeuS / SpyEye / Feodo...but I think it's worth mentioning ;)