ZeuS spreading via Facebook |
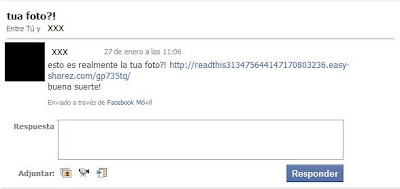
ZeuS is still the talk of the town. It's downloaded through fake antivirus, downloaders and several exploit kits. Of course, the best-known social networking site couldn't be out of this. Last week we could see some Facebook messages like the following:
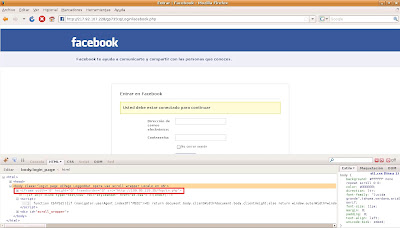
The link in the message would take the users to a Facebook phishing page where they were requested to authenticate. Simultaneously, obfuscated Javascript code was being executed, creating a hidden iframe in the page body:
This iframe redirected the user to another web page with two more iframes:
<iframe g1g="321" src="xd/pdf.pdf" l="56" height="31" width="13">
<iframe g1g="321" src="xd/sNode.php" l="56" height="31" width="13">
After advancing further, we arrived to a directory listing in the same server:
The PDF file intended to be downloaded was a malicious file executing obfuscated Javascript code and containing three vulnerabilities, which were exploited depending on the PDF reader version in use:
The three exploits had identical shellcode:
As it can see seen, the shellcode allowed downloading and launching a binary from the URL of the last image. This binary was a ZeuS sample, version 1.3.2.4, which was installed in the system as sdra64.exe.
On the other hand, the sNode.php file would try to exploit a flash vulnerability through the execution of the nowTrue.swf file after loading in memory a shellcode very similar to the last one, but in this case the binary was downloaded from the following URL:
hxxp://109.95.115.35/fsp/load.php?id=5
This binary had a different MD5, but its behavior was identical, being a 1.3.2.4. version ZeuS too.
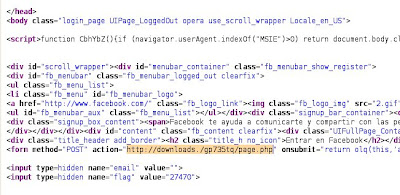
Additionally, when the data requested is filled in the Facebook phishing page they are sent to another URL. At the moment of the analysis this URL contained an incorrect domain, not redirecting correctly:
However, after changing this malformed domain by the IP server, it became possible to get to the desired web page, where a pop-up would inform about the need to upload the Adobe Flash Player version and provide a new binary called update.exe to do it. There was another link in the same page to download another binary, photo.exe, with the same MD5 as update.exe. Both of them have a different MD5 than the rest of commented binaries, but they still have the same behavior: 1.3.2.4 version ZeuS.
If unfortunately any of you have visited any of the mentioned links you can check if you are infected following the tips published some months ago.