Dridex spam campaign using PDF as infection vector |
During this month a Dridex spam campaign using PDF documents as infection vector was spotted. I also received a couple of e-mails in my personal inbox attaching the mentioned PDF files. One of them was using the typical “scanned data” theme (subject was “Scan data” and sender “scanner at eternal-todo.com”) and the other one was related to a confirmation letter (subject was “uk_confirmation_ph764968900.pdf” and the sender “info at calmbeginnings.co.uk”). None of them was really good in social engineering, just adding some words and the attachment.
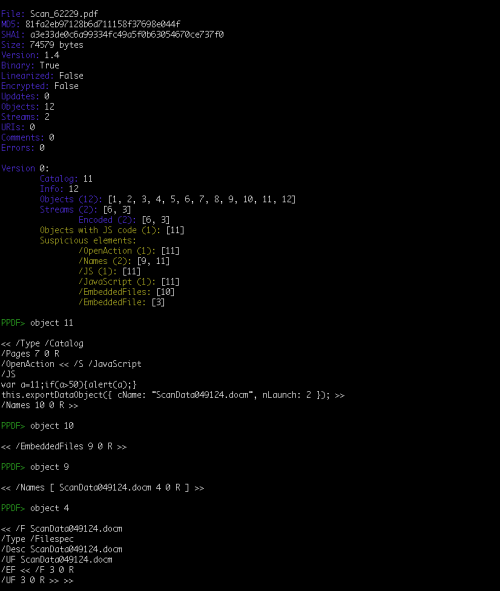
Both PDF documents, named “Scan_62229.pdf” (81fa2eb97128b6d711158f37698e044f) and “uk_confirmation_ph764968900.pdf” (85066792c8952100ac057055a2f49a8c), had a docm file embedded and they were using Javascript code to save and execute the attachment. As you can see in the following image, the exportDataObject function was used using nLaunch=2, which will save the attachment AND open it afterwards without prompting the user for a path. If the argument nLaunch is not present will just save the document on disk, without opening it. Using peepdf's output is quite easy to locate the interesting objects (object 11 for the Javascript code and object 3 for the embbedded document).
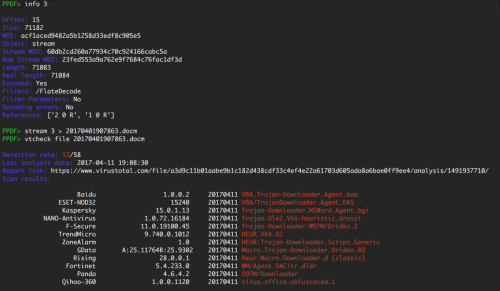
Extracting the docm file with peepdf is as easy as using the “stream” command together with the “greater than” sign to save it on disk. Then we can check VirusTotal with the “vtcheck” command to see if it is detected as malicious or not.
The two docm files extracted from the PDF document, named “ScanData049124.docm” (44edff8fa67eb916fda880de42dad708) and “20170401907863.docm” (60db2cd260a77934c70c924166cabc5a), are Word documents containing macros. This is the typical infection vector used by the cybercriminals nowadays so I will not go into details here. You can use oledump and other tools to extract and analyze the macros.
In this case, the macros were downloading an XORed executable from different URLs, decoding it and executing it to infect the machine. The dropped malware (f1fd0a8e9443710df0859109588eb5fa and 117da8ef79cb0d96c1c803709bd4827f) was Dridex and, more specifically, these were binaries belonging to the botnet 7200. These are the URLs used to download the binaries (some of them still active):
mentalmysteries[.]com/kjv783r
semfamily[.]com/kjv783r
perisoft[.]org/kjv783r
centralsecuritybureau[.]com/874hv
tserv[.]su/874hv
kapil[.]50webs[.]com/874hv
Normally, there is no useful metadata in malicious PDF files, but in this case using the "metadata" command we can see some information. Apparently, the attackers were using iText to create the PDF files and they were created in a country where the time difference is UTC+3. Of course, this information can be faked, but in this case I would say it is accurate ;)
<< /Producer iTextSharp? 5.5.10 ?2000-2016 iText Group NV (AGPL-version)
/CreationDate D:20170410150016+03'00'
/ModDate D:20170410150016+03'00' >>
<< /Producer iTextSharp? 5.5.10 ?2000-2016 iText Group NV (AGPL-version)
/CreationDate D:20170411122518+03'00'
/ModDate D:20170411122518+03'00' >>
In the same way that cybercriminals moved back to use documents with macros to spread malware again, we have seen that they have not forgotten the PDF files as infection vector. PDF documents are still harmless files for lots of users and even if they see warning windows appearing they still click on them and get infected. Luckily, analysts can still use peepdf to have a good time playing with these malicious documents ;) Happy hunting!