ZeuS P2P distribution campaign: ACH transaction canceled |
Our team (S21sec) has detected a ZeuS trojan distribution by email campaign that has been running for some days. The malicious emails include a link to a supposed report about a cancelled transaction, which is actually an HTML page that loads Javascript code into the victim’s browser. This code tries to exploit different vulnerabilities in Java, Flash and PDF to install ZeuS 2.0 on the system. This is one of the latest versions of ZeuS which uses P2P as part of its infrastructure (Murofet 2.0).
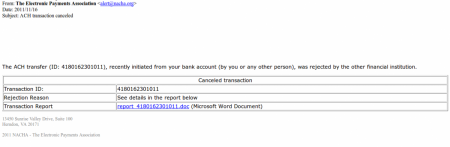
The subject of the emails detected so far is “ACH transaction canceled” and in the body of the mail there is information about a supposed transaction that has been cancelled. If the victim wants further information then they have to visit a link that contains a report about the transaction:
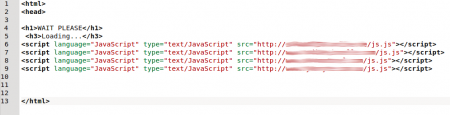
For a few seconds the victim sees a screen indicating that they must wait. Meanwhile 4 scripts, stored on different domains are loaded into user’s browser. They are little more than simple redirections towards the site where the code (that will attempt to perform the exploitation) resides.
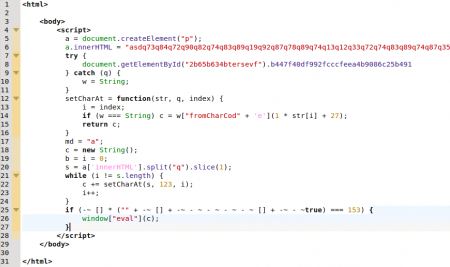
There are currently three different domains hosting the malicious content, created on the 2nd, 6th and 9th of November and they resolve to the same IP, located in Russia. This malicious content is obfuscated Javascript code that belongs to the BlackHole exploit kit.
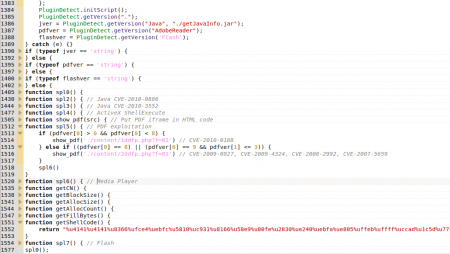
Once the code is “de-obfuscated”, several functions can be seen that attempt to exploit vulnerabilities in various plugins installed in the victim’s browser:
- Java (CVE-2010-3552, CVE-2010-0886)
- Flash
- Media Player
They all use the same (or very similar) shellcode, whose objective is to download and execute the malicious code in question. In the case of the analyzed shellcode, besides executing the binary, stored on the system with a .dll extension, it launches the application Regsvr32 with the parameter -s (silent mode) to try to register the DLL in the system, although the infection has already taken place (the first call to WinExec in the image below).
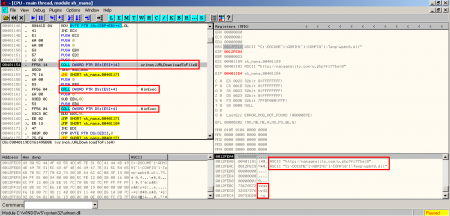
As mentioned before, the downloaded binary is a ZeuS (P2P version). In the second part of this post my colleagues are giving more details (behaviour, affected entities, etc.). Meanwhile update your applications and don’t click on any suspicious links.