Checking if reading an NFC tag is that secure |
As I mentioned in my last post about NFC, we can use NFC Forum tags to store and share information, normally used by marketing departments. This information must have a specific format called NDEF (NFC Data Exchange Format). Thanks to this format different NFC devices can share NDEF messages between them. Each of these messages can store several NDEF records containing different type of information like plain text, images, audio or video (media in general), URIs, etc. You can take a look at the NDEF specification to learn more about it.
Here I'm going to focus on the URI records and their possibilities to perform actions in NFC capable mobile phones when reading this type of tags. The URI specification says that these are the supported schemes:
|
URI Identifier Codes |
Schemes |
|
0x01 |
http://www. |
|
0x02 |
https://www. |
|
0x03 |
http:// |
|
0x04 |
https:// |
|
0x05 |
tel: |
|
0x06 |
mailto: |
|
0x07 |
ftp://anonymous:anonymous@ |
|
0x08 |
ftp://ftp. |
|
0x09 |
ftps:// |
|
0x0A |
sftp:// |
|
0x0B |
smb:// |
|
0x0C |
nfs:// |
|
0x0D |
ftp:// |
|
0x0E |
dav:// |
|
0x0F |
news: |
|
0x10 |
telnet:// |
|
0x11 |
imap: |
|
0x12 |
rtsp:// |
|
0x13 |
urn: |
|
0x14 |
pop: |
|
0x15 |
sip: |
|
0x16 |
sips: |
|
0x17 |
tftp: |
|
0x18 |
btspp:// |
|
0x19 |
btl2cap:// |
|
0x1A |
btgoep:// |
|
0x1B |
tcpobex:// |
|
0x1C |
irdaobex:// |
|
0x1D |
file:// |
We can write these URIs in the NFC Forum tags thanks to a NFC reader/writer like the PN532 board commented in the last post. It's possible to use the library libnfc but this time we are going to play with nfcpy. We can easily modify its helloworld.py script, ignoring some lines and adding these ones to be able to write any URI to our tags (you can download a simple script from here, maybe bogus, take care ;p):
uri = nfc.ndef.Uri.UriRecord(myURI) // Creation of URI Record
uri._data = '\x00'+myURI // 0x00 URI type is any URI
message = nfc.ndef.Message(uri) // Creating the NDEF Message
tag.ndef.message = message.tostring() // Writing to the tag
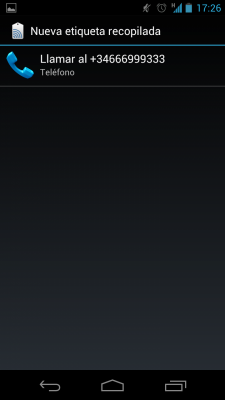
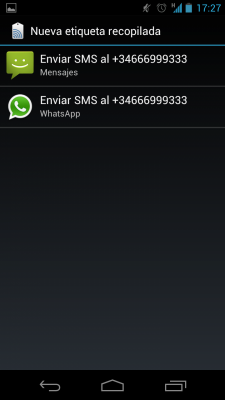
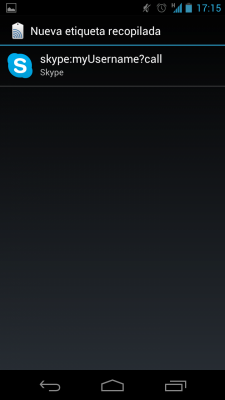
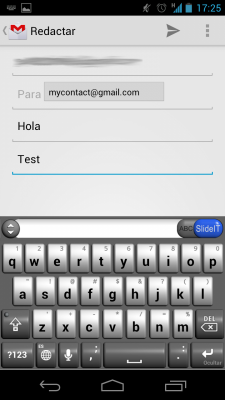
I've performed several tests writing different URIs in the tags and reading them with a Samsung Galaxy Nexus running Android 4.0 (Ice Cream Sandwich). I have also added some other URIs related to well known applications like Facebook, Skype or GTalk. In most of the cases the URI was not recognized by the phone. In other cases the URI was associated to the application but no action was performed, just waiting to the user action. This is the case of “tel:” (phone call), “sms:”, “mailto:”, “file://”, “fb://” (Facebook URI) and “skype:” (Skype URI):
Just in one of the cases, when I included a URI to visit a web site, the phone performed an automatic action: the web browser was launched and it opened the requested URL. It's important to highlight that you don't need to install any app, it's done with the built-in Android NFC reader. You can watch it in the video below where I use NXP TagWriter to write the URL in the tag:
This can be very useful from the commercial point of view. For instance, in Tokyo they are testing this type of advertising in the trains, when the passengers read the NFC tag in the straps then their web browsers open the specific URL. However, from the security point of view I don't think this is a good idea, knowing that this URL can be malicious and can host any kind of exploit. I can remember the QR-Code leading to a Webkit exploit, do you? We could spoof the real tag putting our malicious one in these straps, for example...
Besides writing simple URIs in the tags we can use the SmartPoster format to include some additional metadata like titles, texts, etc. Among these parameter we can find the “action”, useful to indicate if the reader must perform the action specified by the URI automatically, open the application to edit the data or store the data for using later. This could be very dangerous but, fortunately, at least in Samsung Galaxy Nexus this parameter is ignored.
Collin Mulliner has already done some investigations about this and he was able to make some kind of URI spoofing to cheat on the user and make him think that the URI was performing a different action (showing a fake URL, for example). After some quick tests I think there is no much luck with this phone but maybe there are new ways to do it. Let me know if you find any cool stuff ;)
Note: Thanks a lot to my colleague Mikel for lending his mobile phone out to me ;)


Well this is certainly
Well this is certainly interesting. I had no idea that you can spoof the URI on the NFC tags. The security issue with the Tokyo train straps sure seems real, I think they surely must encase the NFC tag within the strap; but then again it would make it hard to change/replace the advertisement. I recently bought some NFC tags from www shop4nfc com and looked into the security concerns. I think that the tags not working unless the phone is unlocked is a good start, but for the time being I think I will keep the NFC tags for personal use and not feel so free to tap my phone wherever it says "Tap Here"... especially after reading your article =)
Thanks for your comment,
Thanks for your comment, Caroline!
Yes, it is better think twice before tapping somewhere with our mobile phone ;)
A related issue; i have one
A related issue; i have one of those cases that you can store a few credit cards. I just realized by storing my commuter debitcard in the case with my phone that the debit card runs via nfc aswell. Sure, this isn't really a problem, but when i found this out, i also realized that the range of my commuter card was greater than that of the normal nfc tags i got with my phone.
This is a big problem when you think about it: how easy would it be to construct a transmitter that fools my phone to belive it just touched a tag? Next time you pull the phone out of your pocket, you realize some malware just bought 50 10-dollar apps on google play or whatnot... The need for more restrictive NFC operational guidelines will, sadly, endanger a really nifty path of usage development for phones, i think. Anyway, i'll keep my NFC turned off until i can replace the proprietary nfc software with something that will ask me for access for every step - with the exception of my personal "trusted" tags, of course...
Hi Martin! Certainly, it
Hi Martin!
Certainly, it would be easy to create custom tags to be read by your phone, but, as you say, the critical issue would be how the apps and the builtin NFC interface manage the data read. I think that normal NFC applications wouldn't allow you to purchase an Android app just by reading an NFC tag. I think there are some security checks before you can do that, but there are other possibilities, depending on the NFC libraries and apps. Anyway, as you say, keep your NFC off when you don't use it, it is a wise option ;)